General Introduction
SharePoint can automatically apply sensitivity labels to a document library. New documents, both created online or uploaded and existing ones (when they are edited), will get the sensitivity label you chose.
If a document label gets manually modified, SharePoint won’t overwrite the label. This isn’t usually an issue because only a few selected number of employees should have the permissions to declassify a document.
This automation supports the following file formats:
- Word: .docx, .docm
- Excel: .xlsx, .xlsm, .xlsb
- PowerPoint: .pptx, .ppsx
- PDF (Preview)
Whilst the support for PDFs is still in preview, I still have yet to have issues with it.
This script was written because I found the steps to enable this feature a bit confusing, and so I wanted to simplify the process with a simple automation.
Before running the script, create and publish your sensitivity labels. You have to publish the label to the user setting the default sensitivity label.
After running the script, go into the labels and modify the scope to include groups and sites. You’ll have to wait a bit between running the PowerShell script and enabling groups and sites, as it’s greyed out by default.
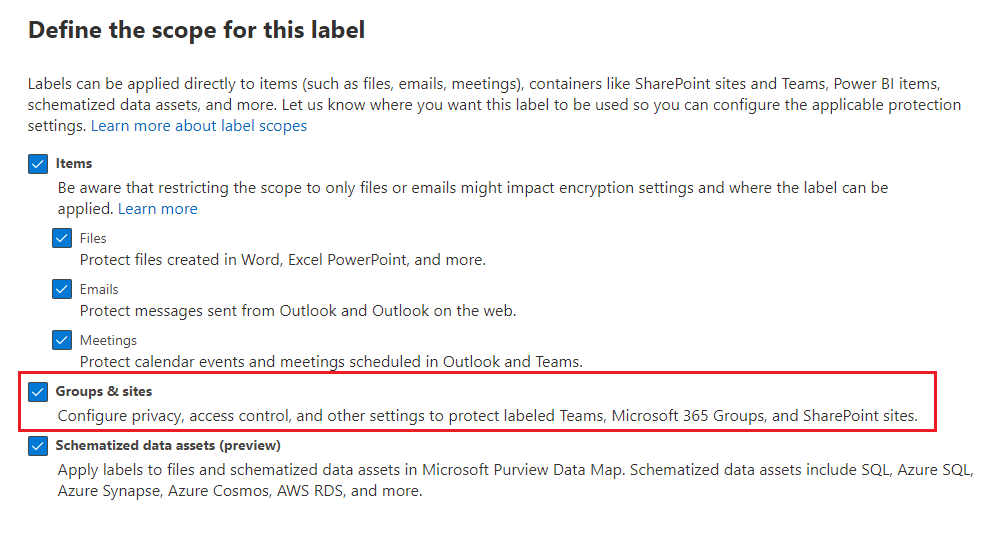
After you have enabled groups & sites, you’ll have to wait for the setting to label a SharePoint library to show up.
To set the default label, go under SharePoint Admin Center, then Sites, Active Sites, and click on the site you wish to apply the sensitivity label to. Under Settings, you’ll find a Sensitivity label dropdown.

Limitations of default sensitivity lables
- By default, documents encrypted by a sensitivity label can only be modified by one person at a time. If you wish to keep co-authoring active and use encryption labels, refer to this post by Microsoft: https://learn.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-coauthoring?view=o365-worldwide
- Doesn’t apply to data at rest, but you can follow my guide to label data at rest automatically: https://azvise.com/2021/12/10/automatically-apply-sensitivity-label-mdfca/
- Double Key Encryption is not supported
- User access to content cannot be configured to anything but Never
- Let users assign permissions is not supported. Labels should be scoped to specific users when using this functionality
The script
I’d suggest updating your SharePoint Online Management Shell before running this script. You can download the new version here:
https://www.microsoft.com/en-us/download/details.aspx?id=35588
Modify the two variables before running the script.
# Define the variables for your enviroment. The first one is the link to your SharePoint Admin Portal. The second one is your administrator account User Principal Name
$SPAdminLink = "https://yourtenant-admin.sharepoint.com"
$AdminUPN = "youradminUPN@contoso.com"
# Connect to SPO. Replace the link with your SharePoint Admin portal
Connect-SPOService -Url $SPAdminLink
# Enable AIP Integration
Set-SPOTenant -EnableAIPIntegration $true
(Get-SPOTenant).EnableAIPIntegration
# Enable support for PDFs. Update SP Online Module if this fails. The link is https://www.microsoft.com/en-us/download/details.aspx?id=35588
Set-SPOTenant -EnableSensitivityLabelforPDF $true
(Get-SPOTenant).EnableSensitivityLabelforPDF
# Connect to AAD and enable support for labels in groups. Source: https://learn.microsoft.com/en-us/microsoft-365/compliance/sensitivity-labels-teams-groups-sites?view=o365-worldwide
Install-Module AzureADPreview
AzureADPreview\Connect-AzureAD
$grpUnifiedSetting = (Get-AzureADDirectorySetting | where -Property DisplayName -Value "Group.Unified" -EQ)
$Setting = $grpUnifiedSetting
# Check if EnableMIPLabels is enabled. If nothing is displayed then you have no group settings. We'll enable it.
$grpUnifiedSetting.Values
# Enable the feature. If it fails check out this guide: https://learn.microsoft.com/en-us/azure/active-directory/enterprise-users/groups-settings-cmdlets#create-settings-at-the-directory-level
$Setting["EnableMIPLabels"] = "True"
# Check that now it's enabled. If it's enabled you'll get
#
#Name Value
#---- -----
#EnableMIPLabels True
$Setting.Values
# Save
Set-AzureADDirectorySetting -Id $grpUnifiedSetting.Id -DirectorySetting $Setting
# Now we'll import ExchangeOnlineManagement and then connect the Compliance Powershell to sync the labels
Import-Module ExchangeOnlineManagement
Connect-IPPSSession -UserPrincipalName $AdminUPN
Execute-AzureAdLabelSync







