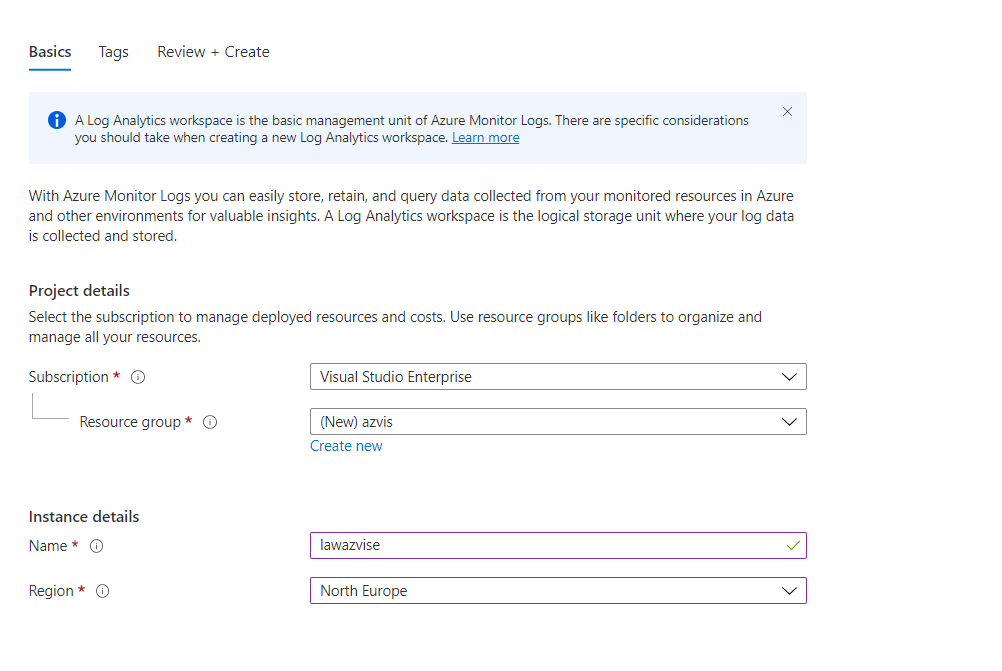
This is a brief and introductory guide on what you may want to configure and change in a basic hardened Teams environment. Please consider that these are just general recommendations, and what works for a company may not be the best for another one. This is especially true when it comes to setting up collaboration services. Keep in mind that your Teams security is only as good as your identity security.
It’s helpful to note that some companies require that users should not be able to create new teams, depending on your internal policies. This is done by limiting the creation of Microsoft 365 groups using the following setting: Groups – Microsoft Azure – Users can create Microsoft 365 groups in Azure portals, API or PowerShell. The same is also available via PowerShell in a more complete way.
Before diving into the settings, you may consider the following, that will not be discussed further, but are non the less important:
- You should already have a basic hardened Azure AD environment (or AD + AAD if you are in an hybrid scenario). Your Teams security will be only as good as your identity security. For example, if you don’t have MFA set up yet or you are not blocking legacy authentication protocols, you might be better off starting from there.
- You should consider setting up retention and expiration policies for Teams, especially if you will let users create teams freely.
- DLP and sensitivity labels should be created and applied.
- You should monitor user activity often via the Teams portal.
- Enhanced encryption policies should be evaluated on a company by company basis since it disables recording and transcription.
- You should start using and configuring Cloud App Security
- Live event policies should be evaluated based on whether your company uses them.
- Voice settings should be evaluated on a customer by customer basis, depending on what you have to implement and your general infrastructure.
Follow along by opening the Teams Admin center and evaluating these settings.
Teams -> Teams settings:
- Turn OFF all external file sharing and cloud file storage options in the Files tab if they are not company approved.
- “Users can send emails to a channel email address” should be set to OFF, or only specified domains should be allowed
- “Scope directory search using an Exchange address book policy” controls how users find and communicate with other people in their organization. This may help users out, but it’s not a “must set”.
Teams -> Teams Policies:
- Consider creating new policies for more granular management. The settings could be left all on if no specific stricter need arises.
Teams -> Teams Update policies:
- You may want to consider setting “Show Office Preview” as not enabled. This is, however, not critical.
Teams -> Teams Upgrade settings:
- Coexistence mode should be set to Teams Only if you are not using Skype for Business.
Users -> Guest access:
- “Make private calls” should be set to OFF since there is mostly no need for a guest to make calls “using” your tenant.
- “Meet Now” should be set to OFF.
- “Edit sent messages” should be set to OFF.
- “Delete sent messages” should be set to OFF.
- “Delete chat” should be set to OFF.
Users -> External access:
- Here, you can either allow all external domains, allow only specific domains or only block specific ones. This setting is very dependent on your organization and your risk acceptance level. Most SMBs are blocking specific domains.
- Allow users in my organization to communicate with Skype users should mostly be set to OFF. The same goes for “People in my organization can communicate with Teams users whose accounts aren’t managed by an organization”.
Teams apps -> Permission policies:
- You either go for a restrictive global policy or create tailored policies later. Whatever is best for your use case.
- Third-party apps should be set to Block all apps if you are not using any.
- Custom apps should be set to Block all apps if you are not using any.
Meetings -> Meeting policies:
- You either go for a restrictive global policy or create tailored policies later. Whatever is best for your use case.
- “Let anonymous people join a meeting” should be set to OFF.
- “Let anonymous people start a meeting” might be set to OFF.
- “Who can present in meetings” should be set to “Organizers, but users can override”.
- “Automatically admit people” should be set to “Invited users only”.
- “Dial-in users can bypass the lobby” should be set to OFF.
Meetings ->Meeting settings:
- Anonymous people can join a meeting should be set to OFF
- Anonymous users can interact with apps in meetings should be set to OFF
- “Insert Quality of Service (QoS) markers for real-time media traffic” is usually set to ON. Not a deal-breaker, but it’s sometimes helpful to get insights.
Meetings -> Messaging policies
- Owners can delete sent messages should be set to OFF if you don’t need moderation in Teams.
- Delete sent messages may be set to OFF, if the need arises.
- Delete chat should mostly be set to OFF.
- Edit sent messages may be set to OFF, if the need arises.
- Read may be set to “Turned on for everyone”, but it’s not a priority.
- Giphy content rating should be set to “Moderate”.
You should set rules under “Notifications & alerts”, as they are more free insights that you get.
If you use Skype for Business, you may want to configure the policies found under Other settings -> Skype for Business.